Want to mitigate fraud? You need to integrate ID proofing, user authentication, and threat detection
Mike Simpson
9th July, 2023 6 min read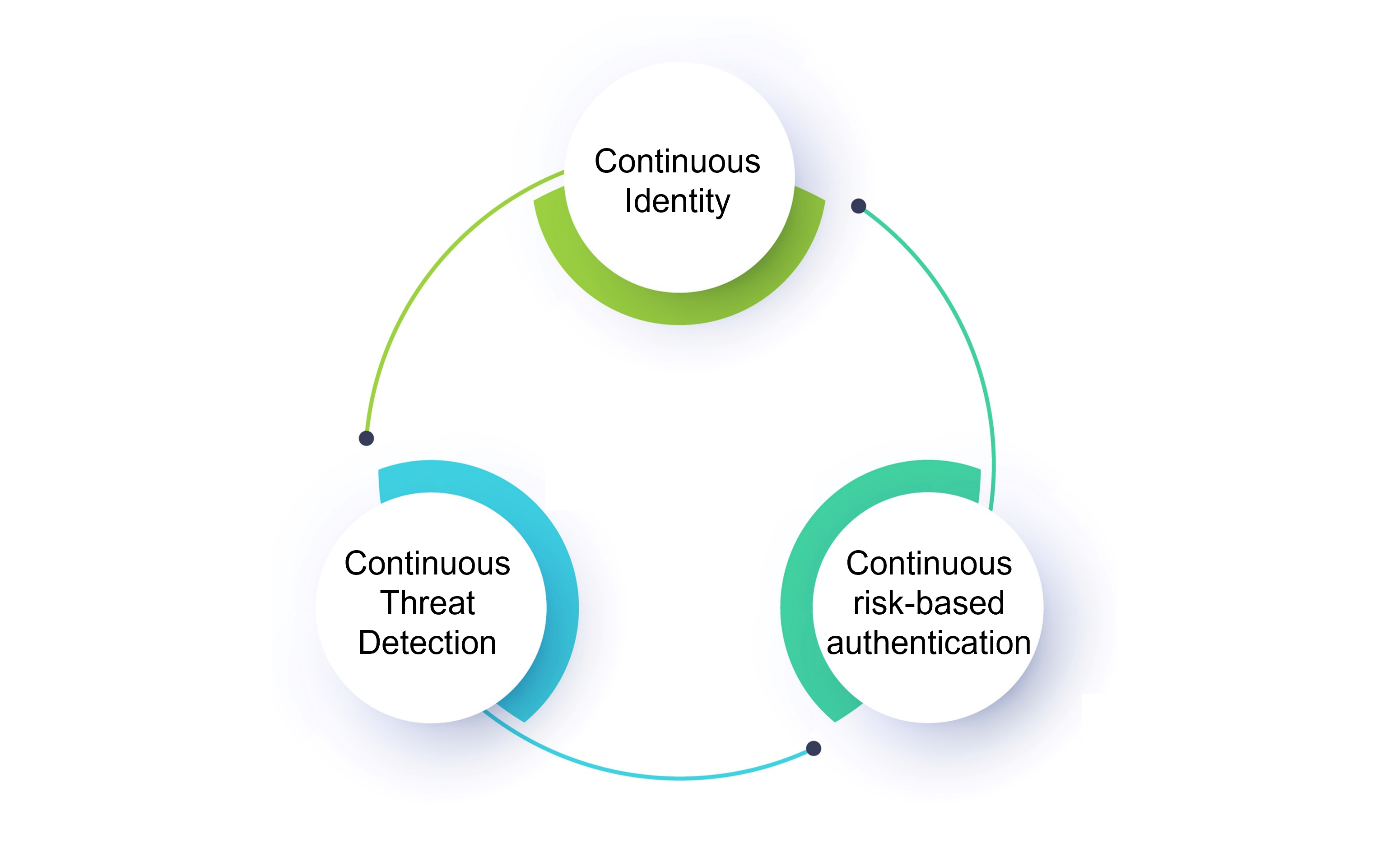
Fraudsters are employing increasingly elaborate techniques to create fake identities and impersonate online users. Deepfake technology is widely accessible and fraudulent actors no longer require deep expertise in data science to execute a deepfake attack. In parallel, enterprise attack surfaces have grown with an increase in apps, APIs, and SaaS services. Even the most advanced enterprises are struggling to defend their resources from attacks on multiple fronts. Increasingly, these enterprises are realizing the advantages of leveraging a wide array of identity proofing, access management, and fraud detection services delivered through orchestration platforms.
Online fraud takes many forms, including account takeover (ATO) fraud, new account fraud, checkout fraud and business email compromise (BEC). Identity proofing, access management, and fraud detection are critical capabilities to deliver a seamless experience for users while defending against multiple attack vectors. Each feature has a role to play in their own right, however fraud mitigation is maximized when they work as a holistic solution.
Identity Proofing
Identity proofing ensures users are who they claim to be by binding their digital identity to their real-life identity. The aim of identity proofing is to prevent fraudulent actors using stolen identity documents, credentials, and personally identifiable information (PII) are used by fraudulent actors to set up new fake accounts. Historically, identity verification has typically been performed during the user onboarding process so the organization has confidence in the authenticity of the user prior to providing access to privileged internal resources. However, many organizations are now realizing that identity is not static. For example, there have been many substantial data breaches where user identity credentials have been stolen. The net result is the impacted user needs to replace their compromised ID documents and the organizations that have relied on those compromised ID credentials need to update their Verification of Identity (VOI) records.
User expectations of the identity proofing process have also changed. It is no longer acceptable to require face-to-face proofing. New users expect to be onboarded through a fully digital experience in less than two minutes. The onboarding user is guided through a simple process of scanning an identity document (eg. passport, driving license, other photo ID) and then taking a ‘selfie’. Behind the scenes, Machine Learning models are employed in realtime to test if the identity document has been falsified. Common ML model tests include photo substitution, font substitution, visual feature anomalies, and text format checks. Facial matching is used to ensure the ‘selfie’ face matches the photo ID face, and the selfie also includes a test of user ‘liveness’ to mitigate the risk of imposter attacks using a photo, video, deepfake, or mask to impersonate the real user. These tests of authenticity are way beyond the capability of human reviewers and they also deliver results in less than 20 seconds, enabling fraud detection to be automated within the online checkout process.
It should be noted that not all identity proofing solutions have these features. Make sure you do negative testing of the service you’re considering to make sure it can detect a range of different fraudulent scenarios such as substituted photos and text on the ID document, and non-live faces during the selfie step.
The importance of rigorous identity proofing cannot be underestimated. We’re seeing a wave of deepfake attacks perpetrated on our clients. Identifying fraudsters while enabling a simple onboarding experience for legitimate users is more important than ever. According to a recent study published by Javelin Strategy & Research, fraudsters stole a jaw-dropping $52 billion in 2021. Perhaps even more concerning for enterprises is the risk posed by Ransomware attackers who try to gain access with stolen credentials. In some cases this threat can be existential.
Access Management and Control
Combining identity proofing with customer access management gives your organization the ability to further enhance security when customers interact with your apps and websites without adding unnecessary friction to the experience. Single Sign On (SSO) allows customers to login with a single set of credentials to access every app and website. This gives your customers a convenient and consistent way to sign-on and lets you reduce the likelihood of a password-related hack. Seamlessly integrating Multi-Factor Authentication (MFA) alongside SSO gives you further confidence in the identity of your customers by continually evaluating risk and context and prompting for additional authentication evidence if needed.
Once users have been verified and authenticated, you want to make sure they only have access to the resources they actually need. Dynamic authorization, also known as attribute-based access control (ABAC) and policy-based access control (PBAC), gives you control over who has access to what data and actions in your SaaS, mobile, web, and enterprise applications. Centralized authorization control and administration makes it easier to create and enforce policies that enhance security, protect resources, and meet regulatory requirements with speed and efficiency.
While traditional Role Based Access Controls (RBAC) has been the norm, its limitations in addressing current use cases and threats makes it less desirable. Policy-based dynamic authorization is more flexible and analyzes contextual attributes in real-time to approve, deny, or step-up authentication requirements prior to a user being able to access resources or make transactions.
The policies an enterprise develops dictate which risk signals should be used during different scenarios, with information being pulled from independent risk providers to determine the next step. A low-risk scenario, such as accessing an app, can remain frictionless while a high-value financial transaction can require stepped up authentication before the transaction is allowed to proceed. For example, a customer who hasn’t used online banking for six months can be required to take an additional authentication step before being allowed to transfer $5,000 to a suspicious account to ensure the person trying to make the transfer is the legitimate account owner and not a fraudster.
Threat Detection
Detecting fraudulent behavior before an action or transaction occurs also limits financial and reputational damage. Online fraud detection tools use Artificial Intelligence (AI) and Machine Learning (ML) to recognize suspicious behavior and prevent fraudsters from creating accounts, logging in, and/or completing transactions.
The behavior of customers, employees, and partners follows predictable patterns that aren’t replicated by bots and hackers, such as typing at a normal speed rather than copying and pasting data at fast rates. Speed is usually a high priority for bad actors when they attempt to access as many accounts as possible in a short period of time using brute force attacks or credential stuffing with compromised credentials.
Collecting and analyzing multiple data points about behavior on an ongoing basis helps identify new threats as they develop. Fraud detection and monitoring tools can be customized for your organization, with risk assessments looking at data points such as:
- Device type, operating system, and version
- Browser type and version
- Date, time, and location of authentication
- Transaction history
- Behavioral history
The nature of this contextual data highlights the synergies between identity proofing, authentication, and threat detection. The threats are informed by authentication history and in turn dictate the level of authentication required. And in situations where the threat is significant, it may be necessary to update identity proofing for the user.
Convergence of Identity Proofing, Access Management, and Threat Detection
Bad actors are constantly looking for new ways to enter and exploit your organization. Successfully combating online fraud requires an integrated approach across Identity Proofing, Access Management, and Threat Detection. For many organizations these functions reside in separate silos, managed by different teams and leveraging separate 3rd party solutions. No one wants to overburden developers with the coding nightmare of integrating these disparate systems. Moreover, trying to integrate solutions from multiple vendors can be costly, time consuming, and lead to vulnerabilities, fraud, data breaches, and ransomware. Organizations need a roadmap that leads to a low or no-code solution that saves time, money and frustration.
Truuth is an orchestration platform that allows you to pick and choose the best options for identity proofing, user authentication, and threat detection. Low or no-code solutions enable simple deployment in a wide range of organization settings. Contact us to learn more about our comprehensive solution that incorporates identity proofing, access management and online fraud detection.
Next article
The risks of ChatGPT for identity fraud
Fraudsters are employing increasingly elaborate techniques to create fake identities and impersonate online users. Deepfake technology is widely accessible and fraudulent actors no longer require.
